Introduction
In some of the last few articles I've talked about types between IRIS and Python, and it is clear that it's not that easy to access objects from one side at another.
Fortunately, work has already been done to create SQLAlchemy-iris (follow the link to see it on Open Exchange), which makes everything much easier for Python to access IRIS' objects, and I'm going to show the starters for that.




.png)
(1).png)

.png)
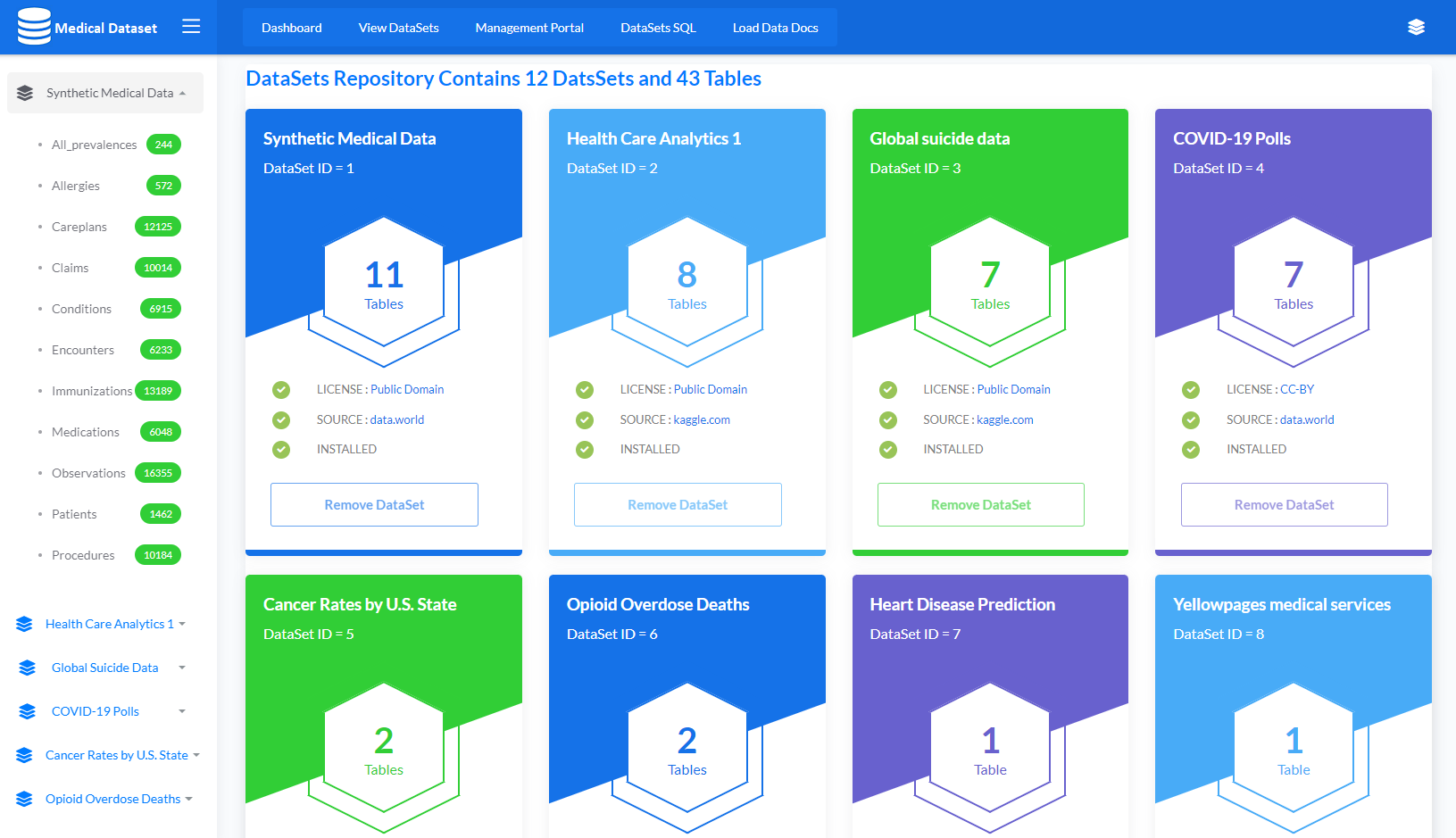
 In the previous parts (
In the previous parts (