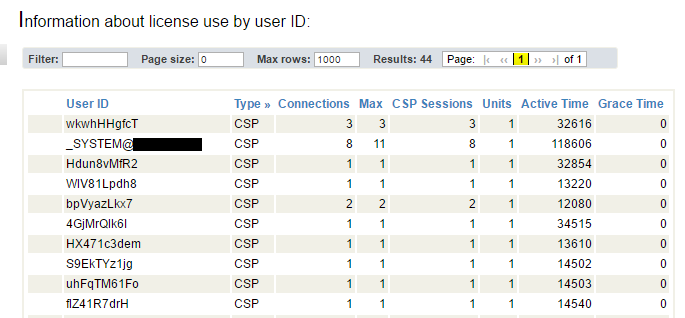
Hi ,
i installed and configure the cache odbc ODBC-2016.1.1.107.0-lnxrhx64.tar in centos7.
it connected while executing in terminal .(i.e isql -v DSN)
odbc_connect work in executing php shell script in terimal.
but odbc_connect not working in PHP web applcation.
Thanks,
Prabakran A.