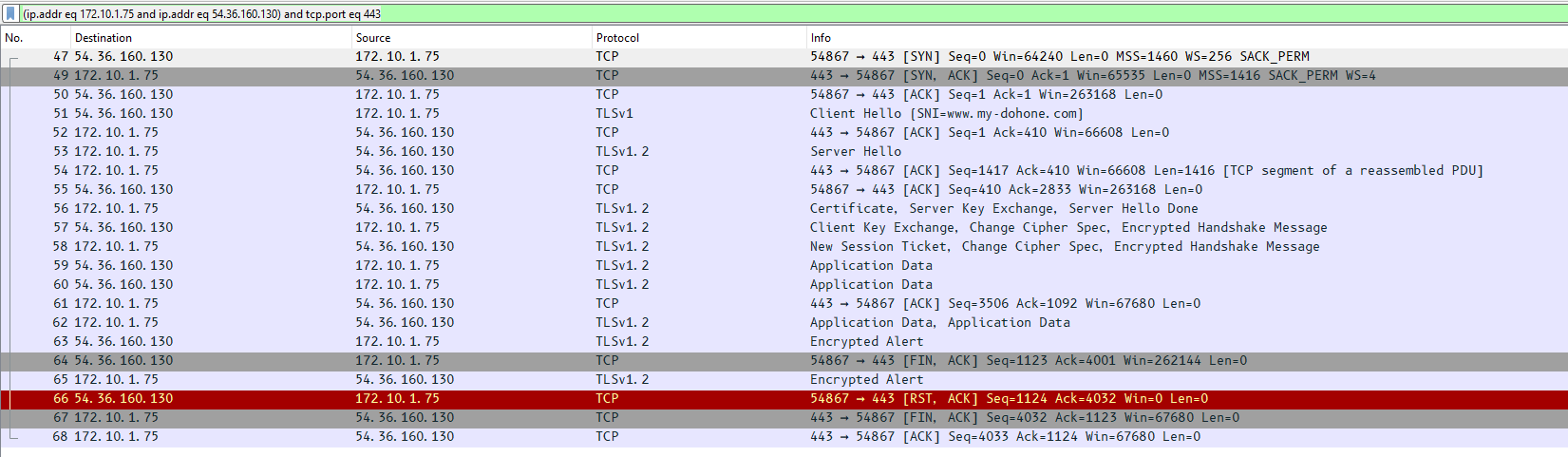
What is JWT?
JWT (JSON Web Token) is an open standard (RFC 7519) that offers a lightweight, compact, and self-contained method for securely transmitting information between two parties. It is commonly used in web applications for authentication, authorization, and information exchange.
A JWT is typically composed of three parts:
1. JOSE (JSON Object Signing and Encryption) Header
2. Payload
3. Signature

.png)