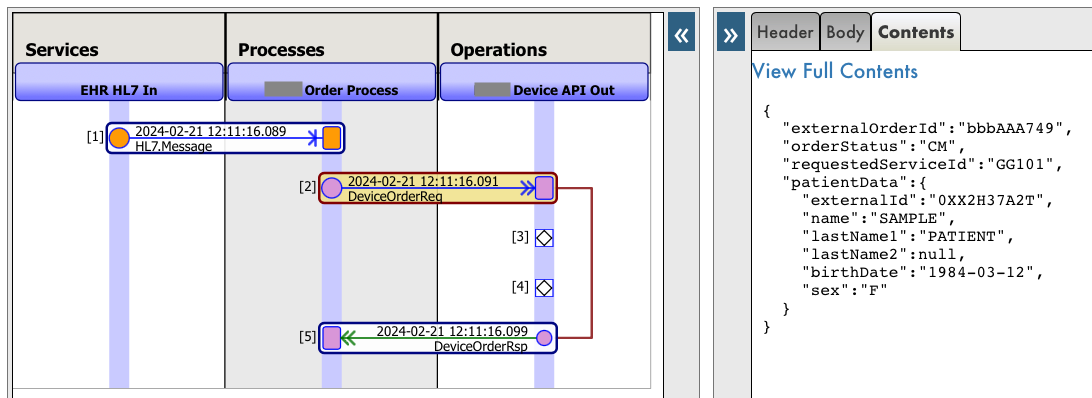
Introduction
InterSystems IRIS allows you to build REST APIs using ObjectScript classes and the %CSP.REST framework. This enables the development of modern services to expose data for web apps, mobile apps, or system integrations.
In this article, you'll learn how to create a basic REST API in InterSystems IRIS, including:
- A persistent data class
- A REST class with
GETandPOSTmethods - A web application to expose the API
-
A full demonstration using Docker
.png)
.png)

.png)
.png)