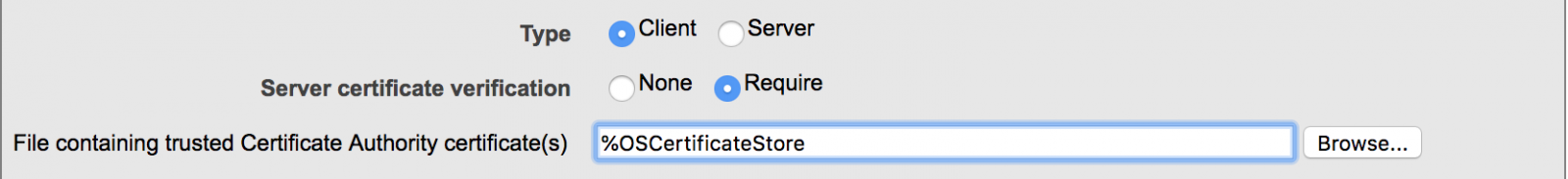
Hi Community,
I am configuring new SSL Configuration for Gmail (For sending errors to gmail in ensemble production) by following the below steps.
Step1:
.png)
Step2:Giving the server address smtp.gmail.com
Step3:Giving the port number , I have tried giving 465,587,25 as port number still is not connecting
Can anyone please tell me where i am doing wrong on configuration?
Thanks,
Saroja.A

 I unable to change response Class.
I unable to change response Class.
.png)