Hi Developers,
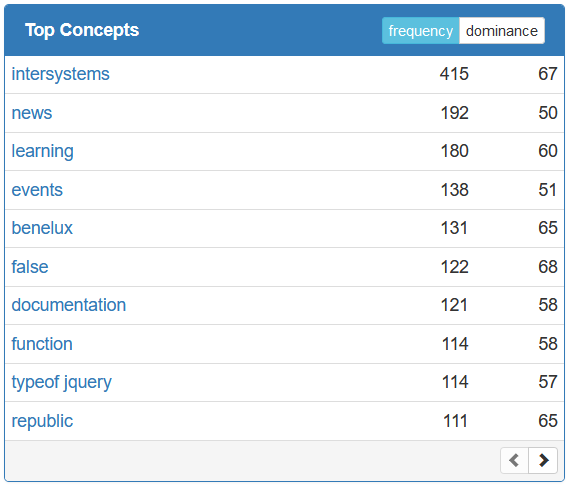
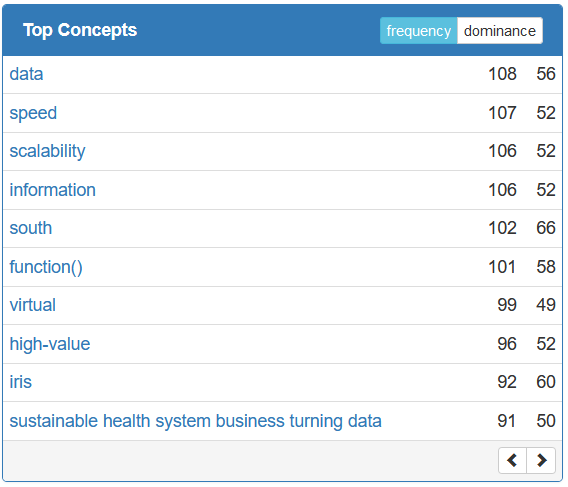
This post is a compilation of Top Authors, Top Experts and Top Opinion Makers of the InterSystems Developer Community in 2019. And it is a good guide "Who to Follow" in 2020.
We're glad to present these people who have contributed a lot to our community in 2019.

Let's take a closer look at the DC Wall of Fame 2019 and greet everyone with big applause! 👏🏼





.png)