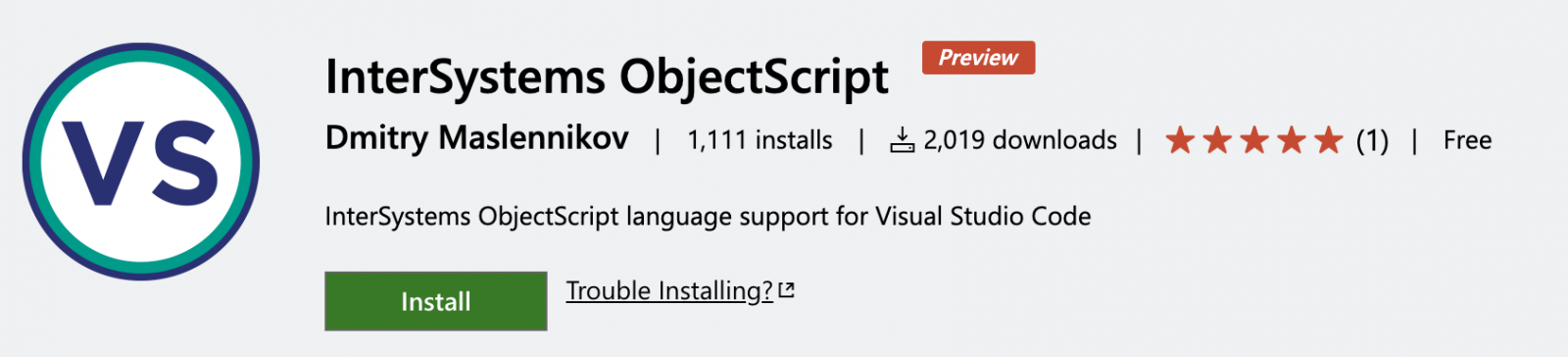
My extension has recently reached first 1000 installations. And thank you all of you, who use it and fill issues and even contribute to the project.
The latest version of the extension already has more not yet announced features. I'm going to make this announcement later.
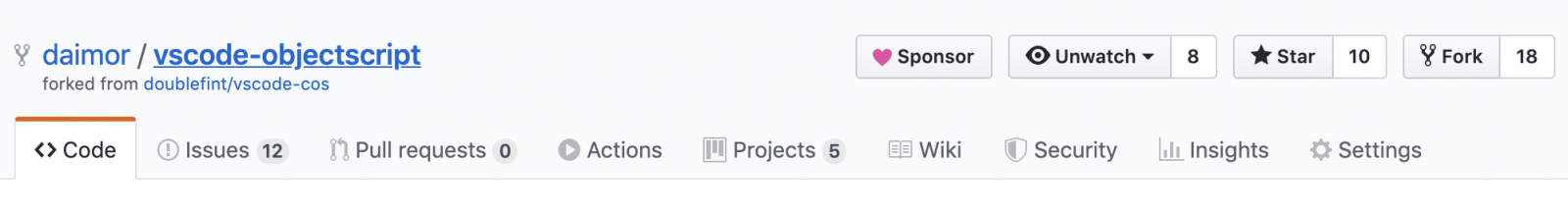
Sometime ago GitHub announced their new feature - sponsoring OpenSource projects stored on GitHub.
I would like to invite you to donate to the project if you found it useful for you or just wanted to support it.
You can do it by clicking the new Sponsor button appeared on GitHub.
Fill free to contact me directly, if want other

.png)

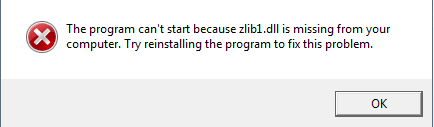 How to fix it?
How to fix it?