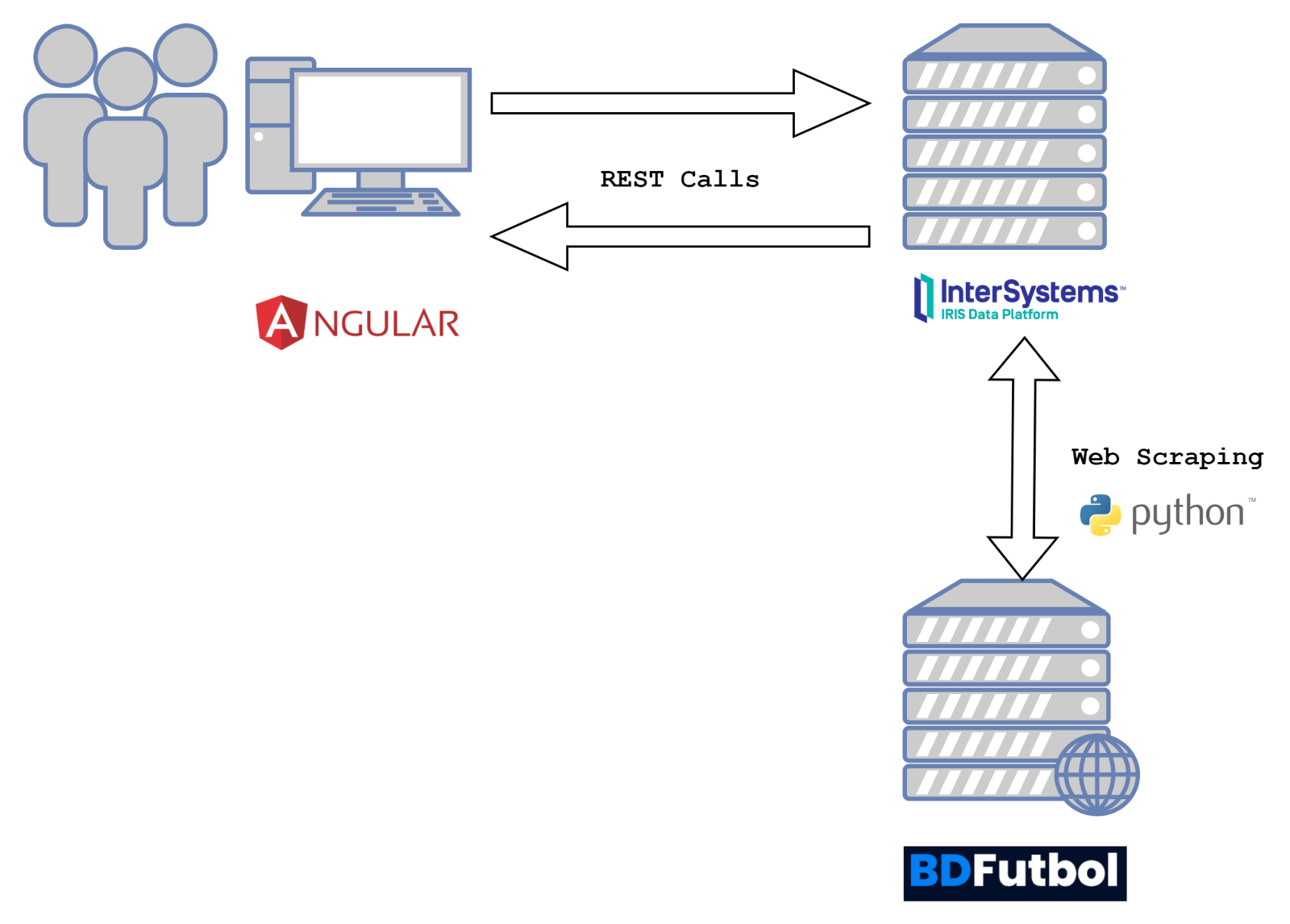
Created by Daniel Kutac, Sales Engineer, InterSystems
Warning: if you get confused by URLs used: the original series used screens from machine called dk-gs2016. The new screenshots are taken from a different machine. You can safely treat url WIN-U9J96QBJSAG as if it was dk-gs2016.
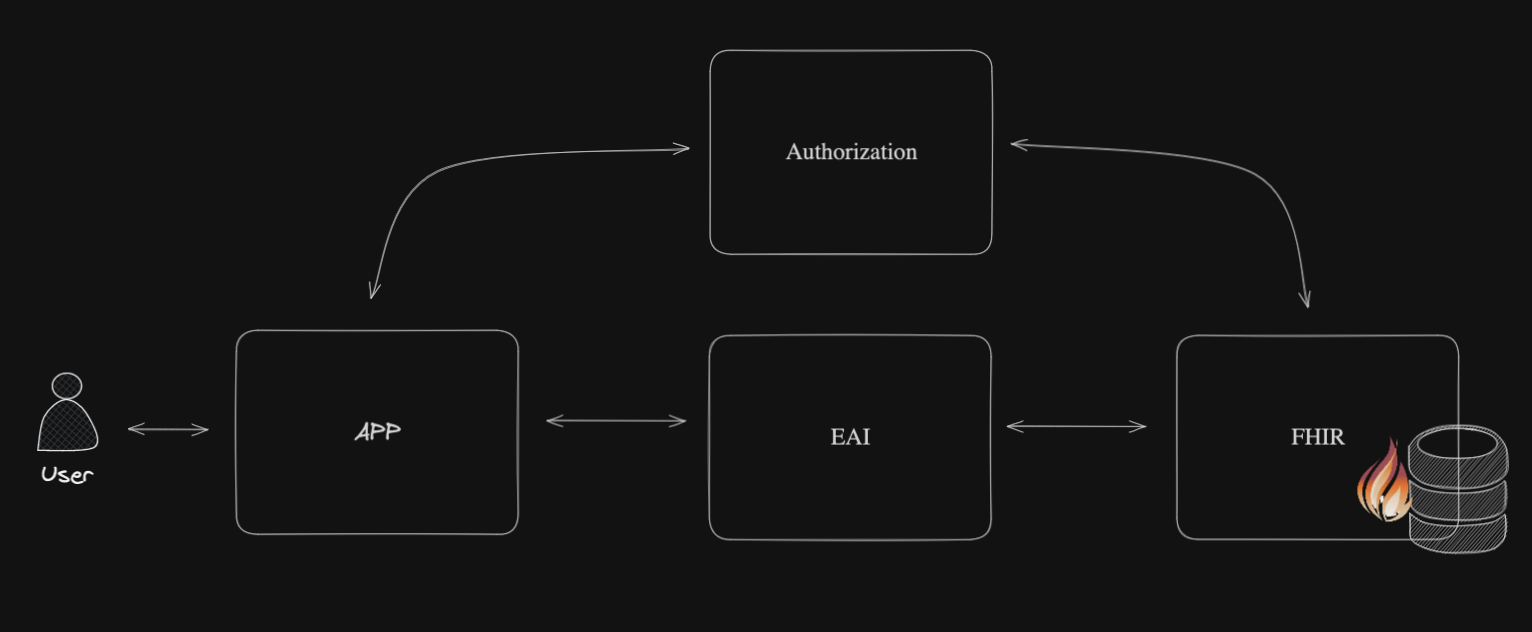
Part 2. Authorization server, OpenID Connect server

 In the
In the 
.png)