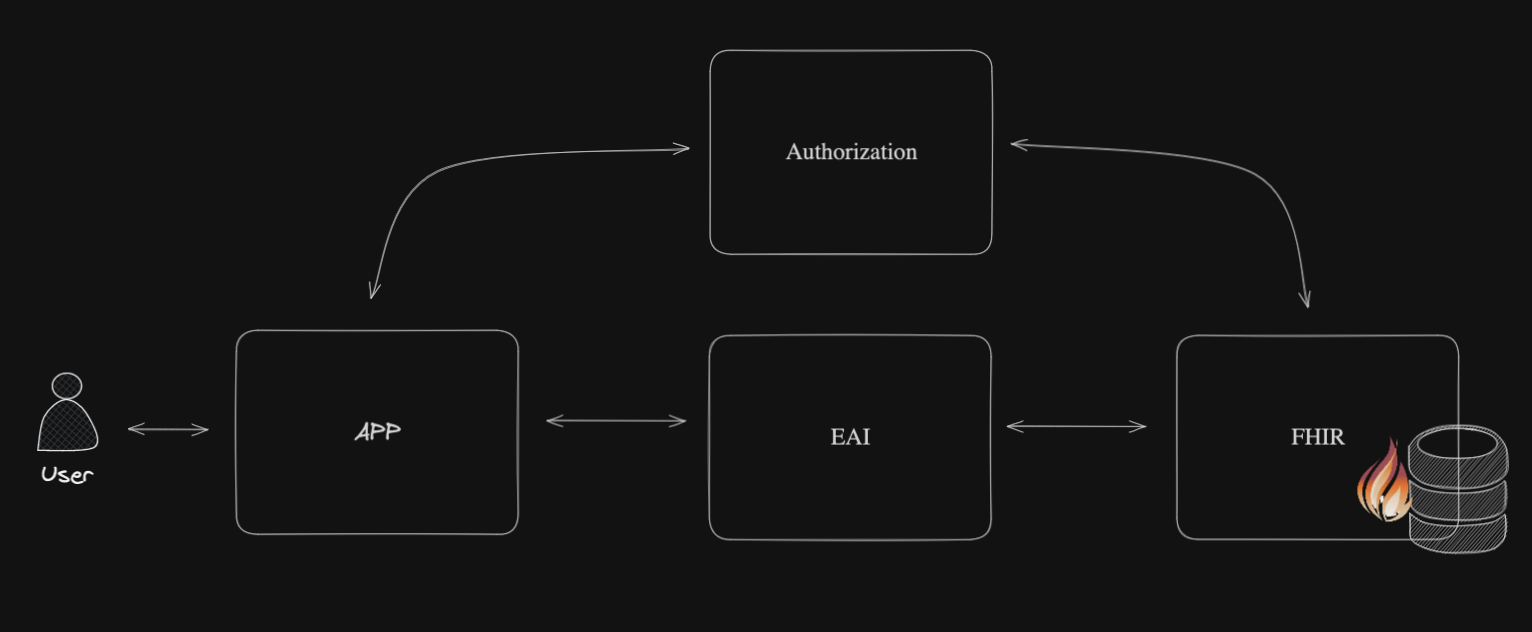
Over the past couple of months, I have been working on the SMART on FHIR EHR Launch to test the capabilities of IRIS for Health using two open-source apps from CSIRO: SMART-EHR-Launcher and SMART Forms App. This journey has been incredibly interesting, and I’m truly grateful for the opportunity to work on this task and explore more of IRIS for Health’s potential.

.png)