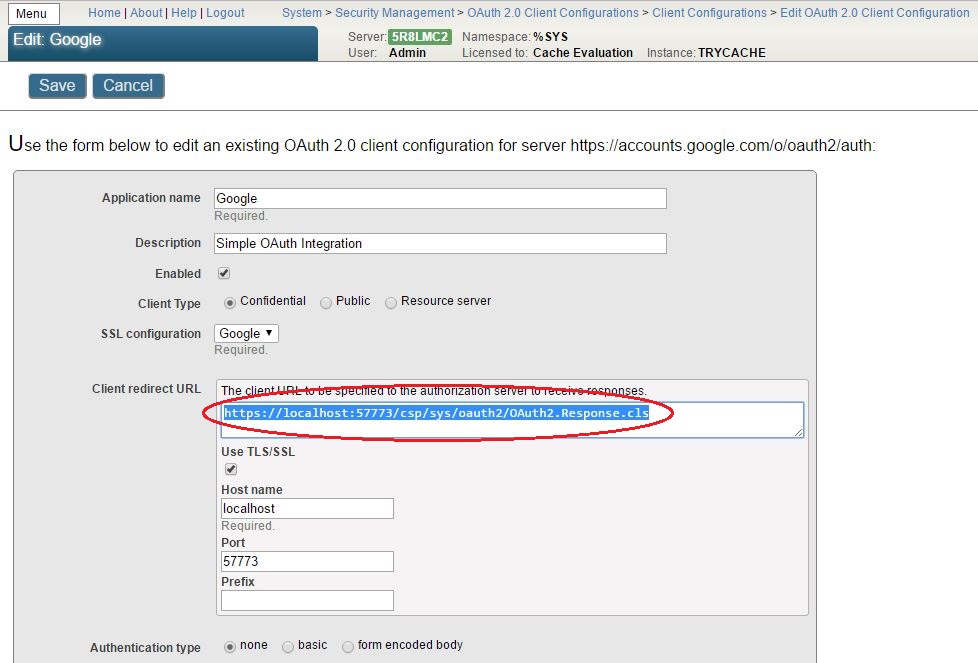
I am trying to find documentation on how Cache Studio locks a Routine/Class a developer is editing.
On the flip side, I am looking for documentation on how Atelier does the same.
Ultimately I am looking for the differences and what happens if both Studio and Atelier through different developers go after the same Routine/Class.
I am not asking for an answer (however that would be nice), I am looking for pointers to documentation.
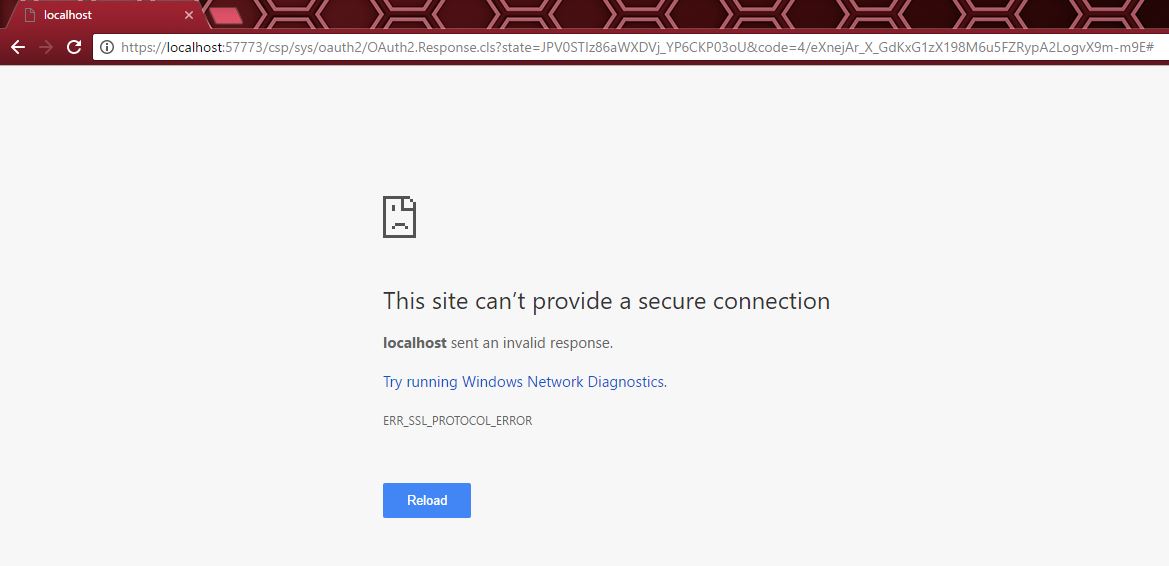 I unable to change response Class.
I unable to change response Class.