In this article I will demonstrate the following :
- Update ReferencesRange(OBX:7) against ObservationIdentifier(OBX:3.1)[TestCode] from database by using custom utility function
- Update Abnormal Flag(OBX:8) against ObservationIdentifier(OBX:3.1)[TestCode] and ObservationValue(OBX:5)[Result] from database utility function
- Route Message based on Abnormal Flag(OBX:8)
Below is the primary and transformed HL7 2.5 ORU_R01 message: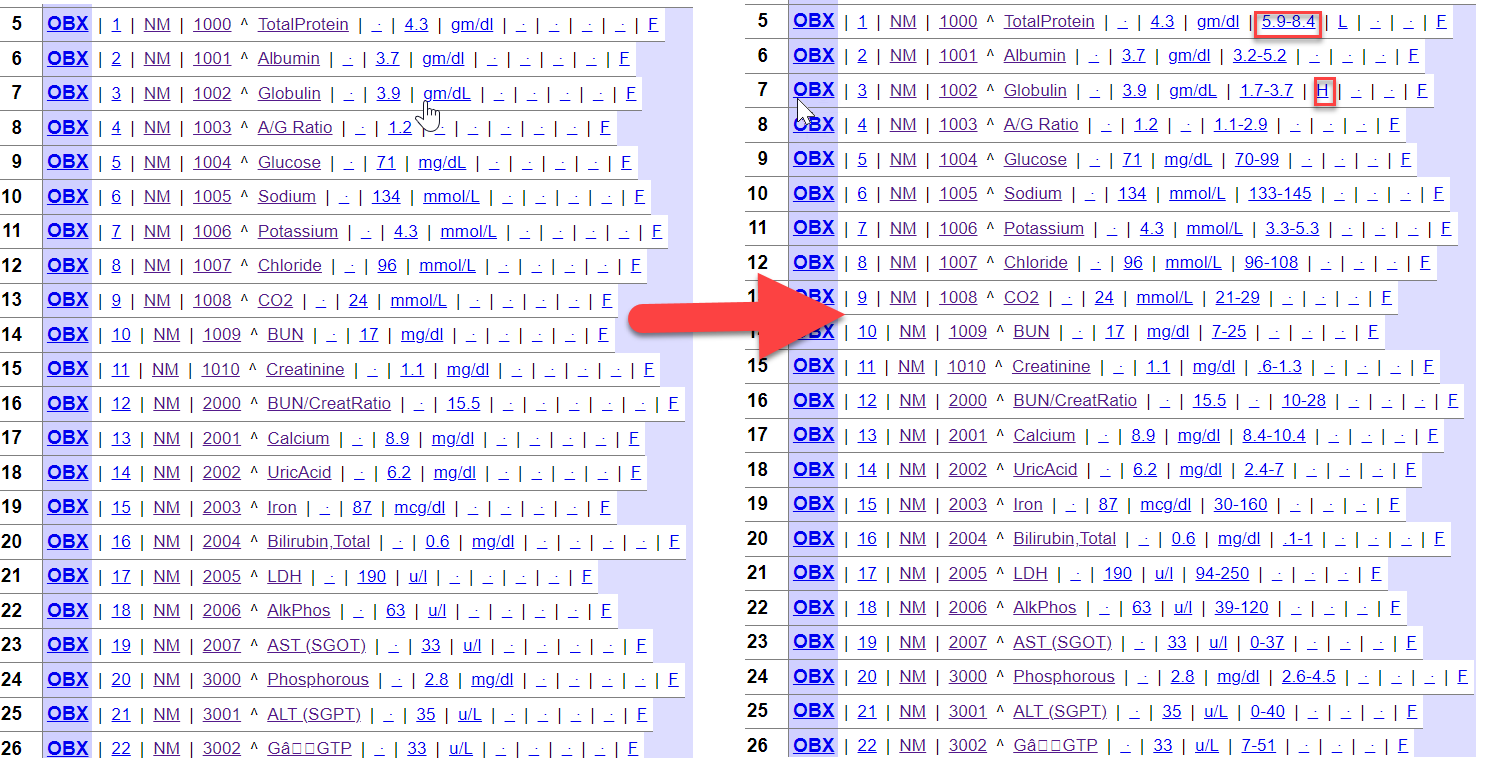

.png)