When you first start working with InterSystems IRIS, it’s a common practice to install a system with only a minimum level of security. You have to enter passwords fewer times and this makes it easier to work with development services and web applications when you're first getting acquainted. And, sometimes, minimal security is more convenient for deploying a developed project or solution.
And yet there comes a moment when you need to move your project out of development, into an Internet environment that’s very likely hostile, and it needs to be tested with the maximum security settings (that is, completely locked down) before being deployed to production. And that’s what we’ll discuss in this article.
For more complete coverage of DBMS security issues in InterSystems Caché, Ensemble, and IRIS, you may want to read my other article, Recommendations on installing the InterSystems Caché DBMS for a production environment.
The security system in InterSystems IRIS is based on the concept of applying different security settings for different categories: users, roles, services, resources, privileges, and applications.
 Users can be assigned roles. Users and roles can have privileges on resources — databases, services, and applications — with varying read, write, and use rights. Users and roles can also have SQL privileges on the SQL tables located in databases.
Users can be assigned roles. Users and roles can have privileges on resources — databases, services, and applications — with varying read, write, and use rights. Users and roles can also have SQL privileges on the SQL tables located in databases.
 Hello to all developers and IRIS users.
I am submitting to the competition a project for an alternative IRIS management portal that I have long wanted to create. The project was implemented on the Django framework and the
Hello to all developers and IRIS users.
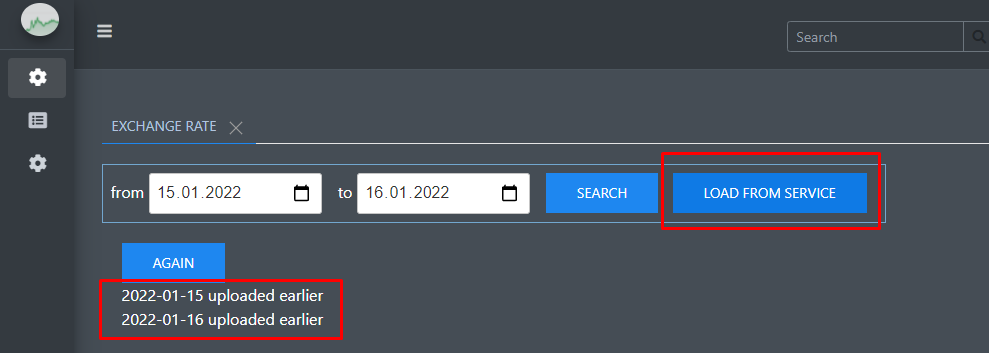
I am submitting to the competition a project for an alternative IRIS management portal that I have long wanted to create. The project was implemented on the Django framework and the  This project is implemented as a tool for viewing temperature data taken from a temperature sensor installed in Rasperry PI and located in a remote place where there is Internet, for example, in
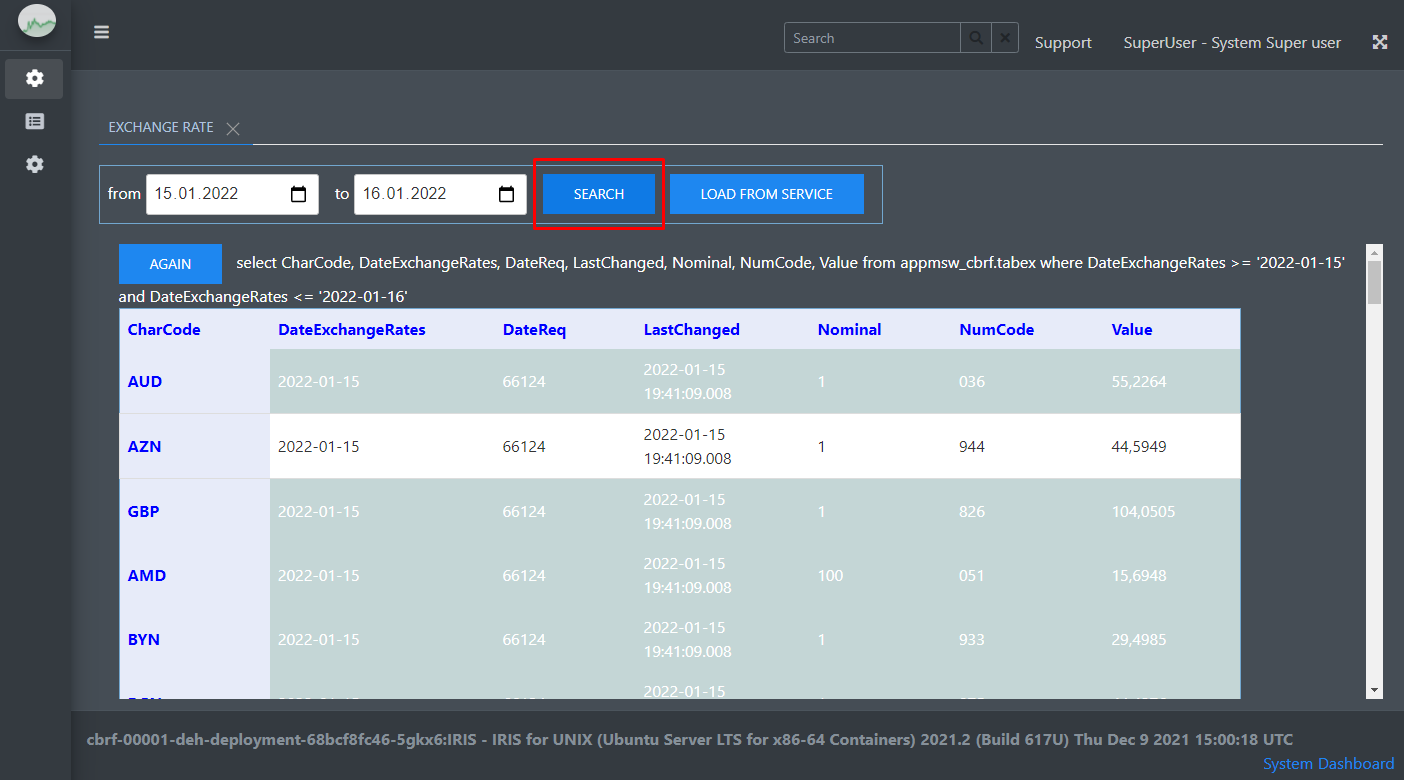
This project is implemented as a tool for viewing temperature data taken from a temperature sensor installed in Rasperry PI and located in a remote place where there is Internet, for example, in 
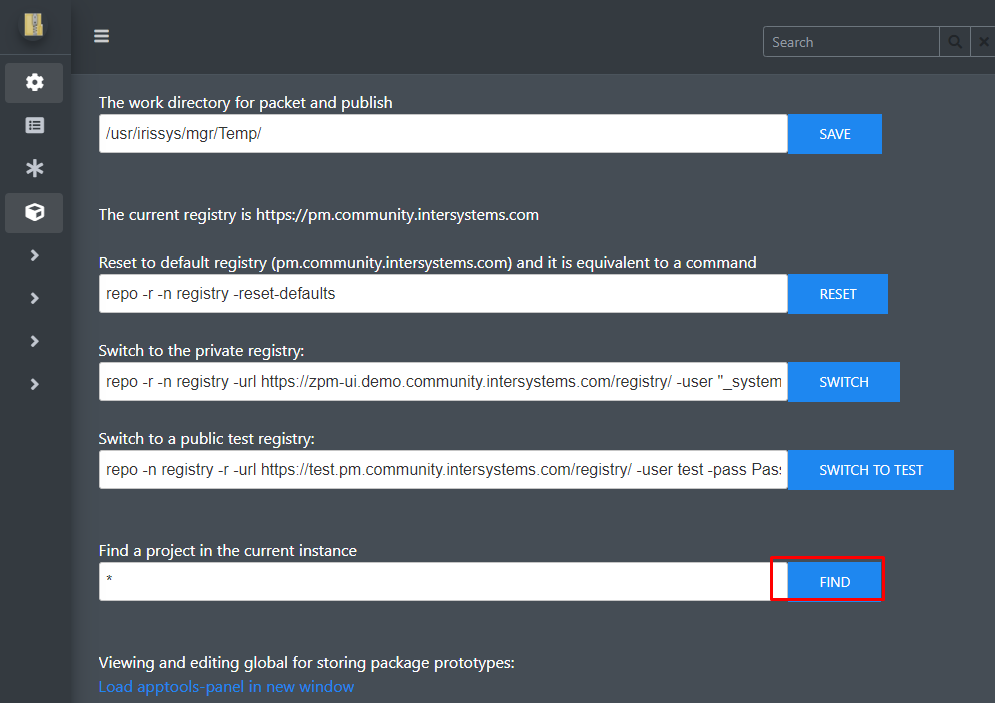
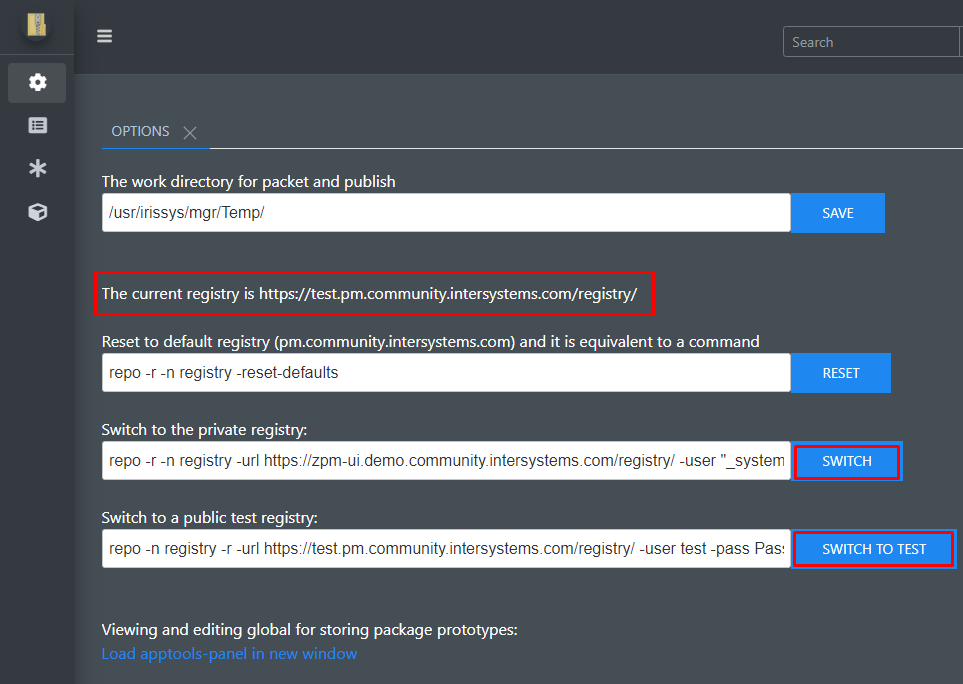
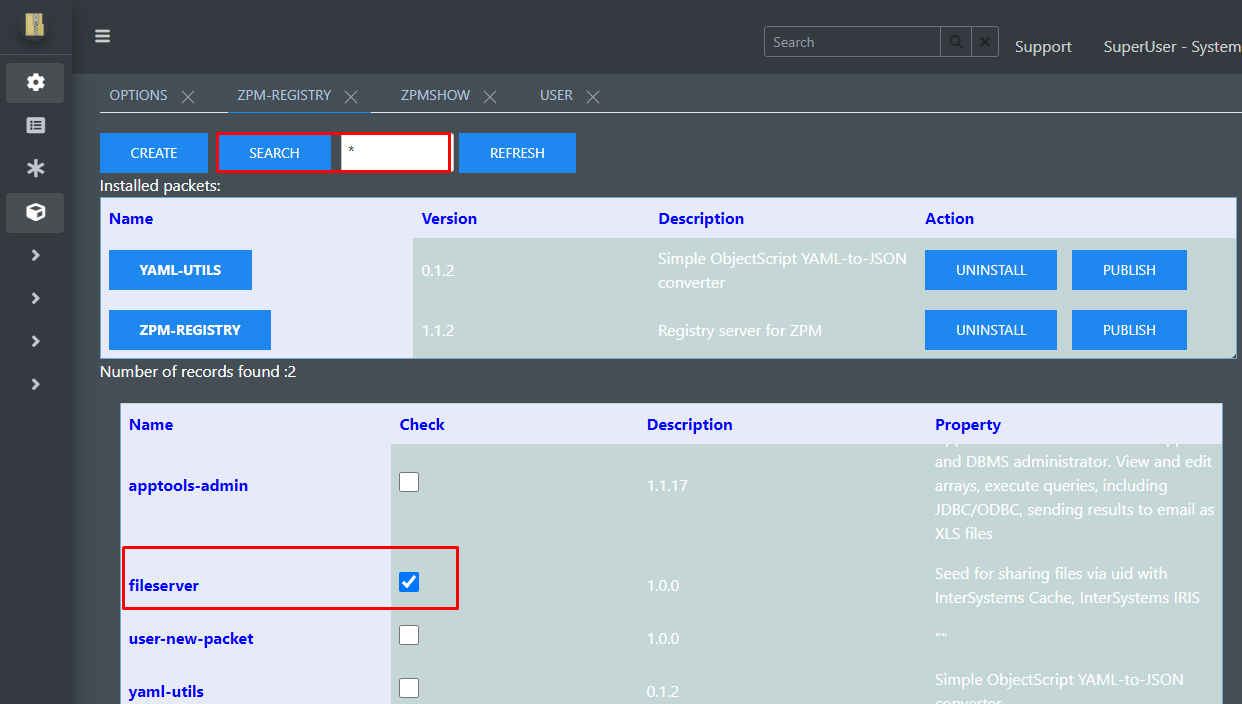
 Looking at my
Looking at my  I recently published
I recently published  Developing the project
Developing the project