Hey folks! Having recently onboarded to InterSystems, I realized that despite having a totally free and awesome Community Edition, it's not super clear how to get it. I decided to write up a guide highlighting all the different ways you can access the Community Edition of InterSystems IRIS:
Get InterSystems IRIS Community Edition as a Container
Working with a containerized instance of the Community Edition is the recommended approach for folks who are new to developing on InterSystems IRIS, and in my opinion it's the most straightforward. InterSystems IRIS Community Edition can be found on DockerHub; if you have an InterSystems SSO account, you can also find it in the InterSystems Container Registry.
In either case, you'll want to pull the image you want using the docker CLI:
docker pull intersystems/iris-community:latest-em
// or
docker pull containers.intersystems.com/intersystems/iris-community:latest-em
Next, you'll need to start the container: In order to interact with IRIS from outside the container (for example, to use the management portal) you'll need to publish some ports. The following command will run the IRIS Community Edition container with the superserver and web server ports published; note that you can't have anything else running that depends on ports 1972 or 52773!
docker run --name iris -d --publish 1972:1972 --publish 52773:52773 intersystems/iris-community:latest-em
Get InterSystems IRIS Community Edition in the Cloud
You might want to avoid having to deal with a local installation entirely; if that's the case, you can get up and running with a cloud deployment of InterSystems IRIS Community Edition. All major cloud providers are supported; check our Cloud Partners page for more information. For this example, we're going to focus on deploying on AWS.
Start by finding the InterSystems IRIS Community Edition on the AWS Marketplace:
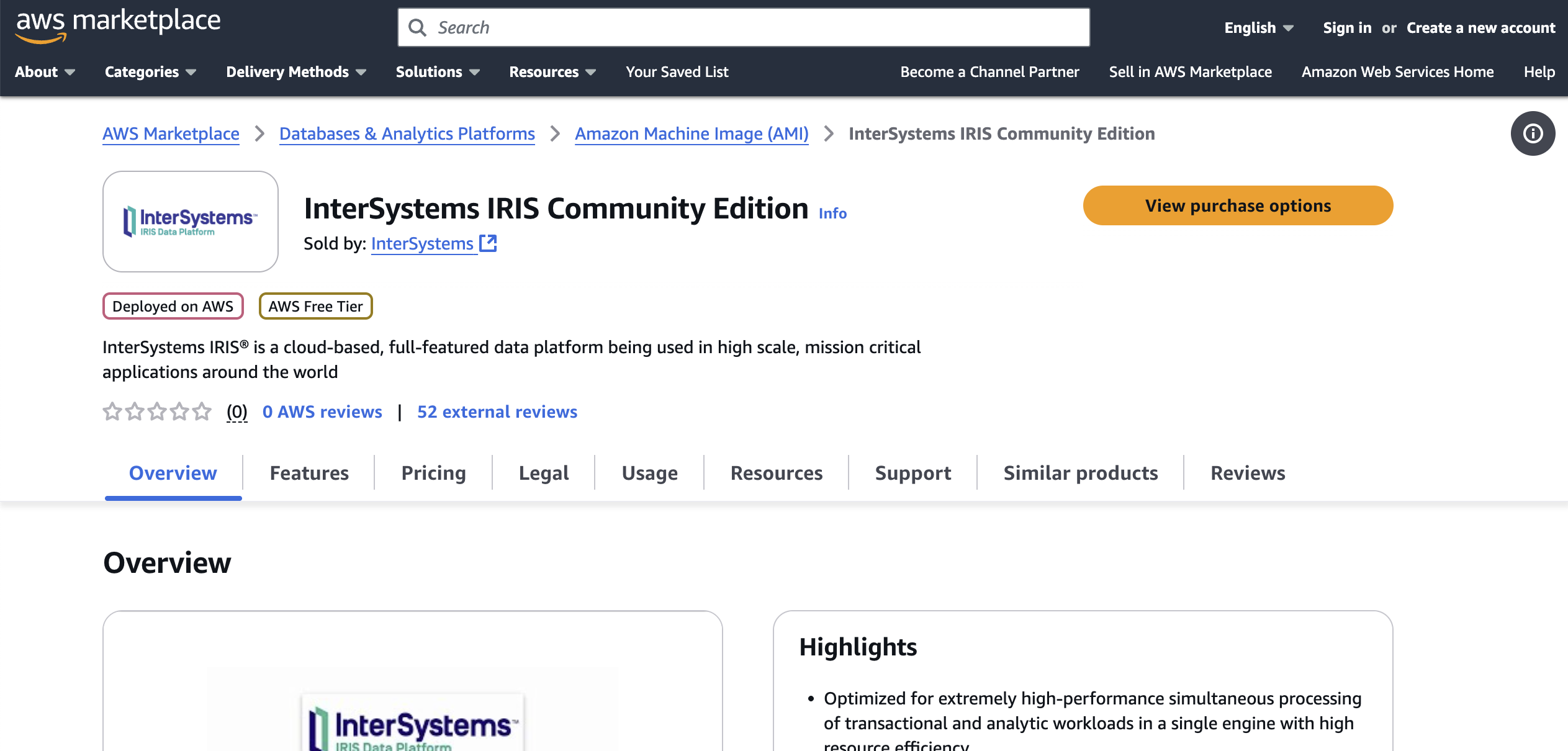
You can click "View purchase options" and log into your account to view the subscription page:
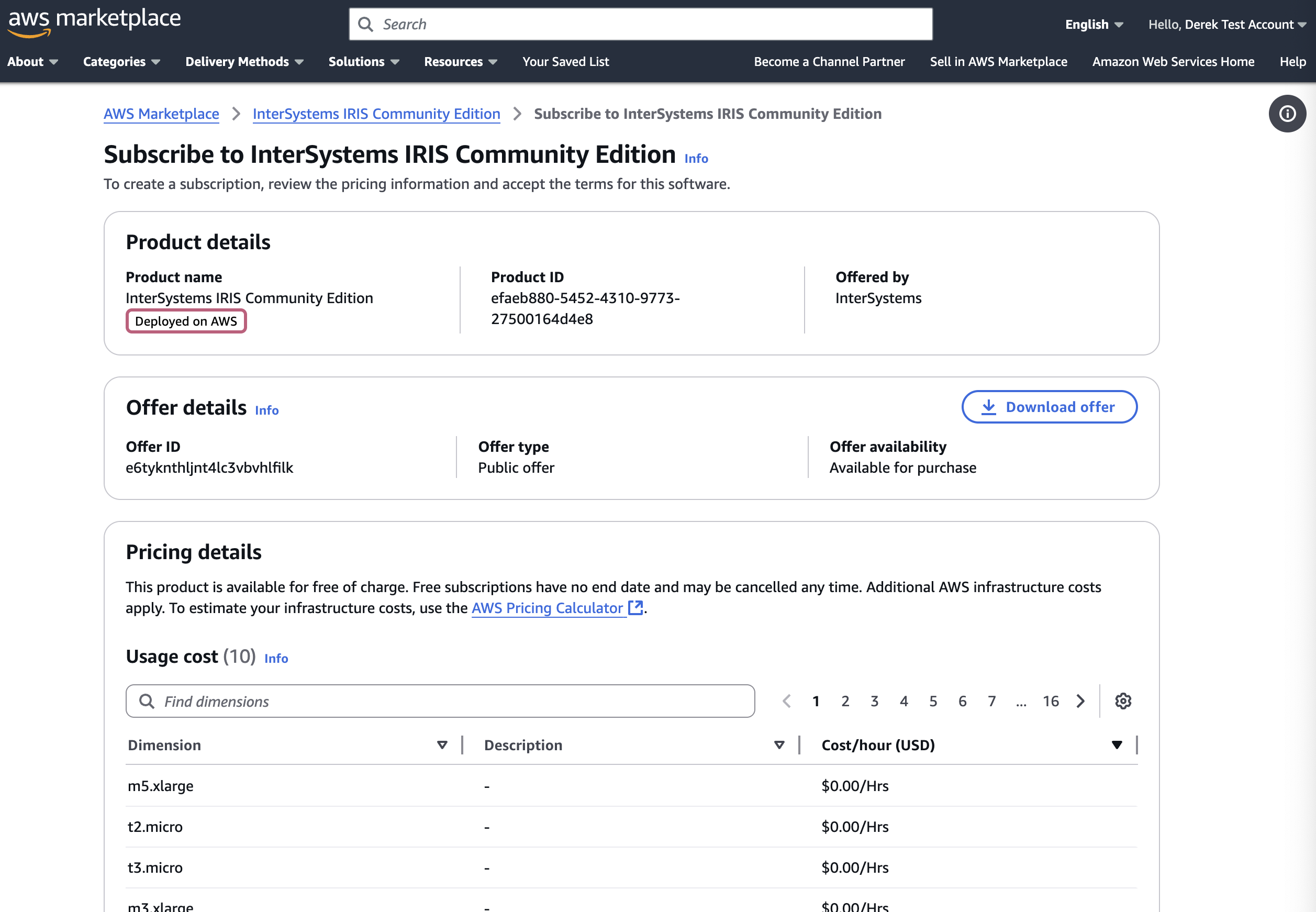
Scrolling down, you can click "Subscribe," fill out the required information, and then click "Deploy" to deploy the IRIS Community Edition as a cloud node! Check out our documentation on deploying InterSystems IRIS to the cloud for more information.
Get InterSystems IRIS Community Edition as an Install Kit
If you prefer to work with InterSystems IRIS installed directly to your machine and you don't want to deal with containers, you can download an install kit for your system from the InterSystems Evaluation Service. In order to download an install kit, you'll need an InterSystems SSO login; the good news is, if you have an account here on the Developer Community you already have one! Otherwise, you can click "Register for a new account" and complete the steps that follow:
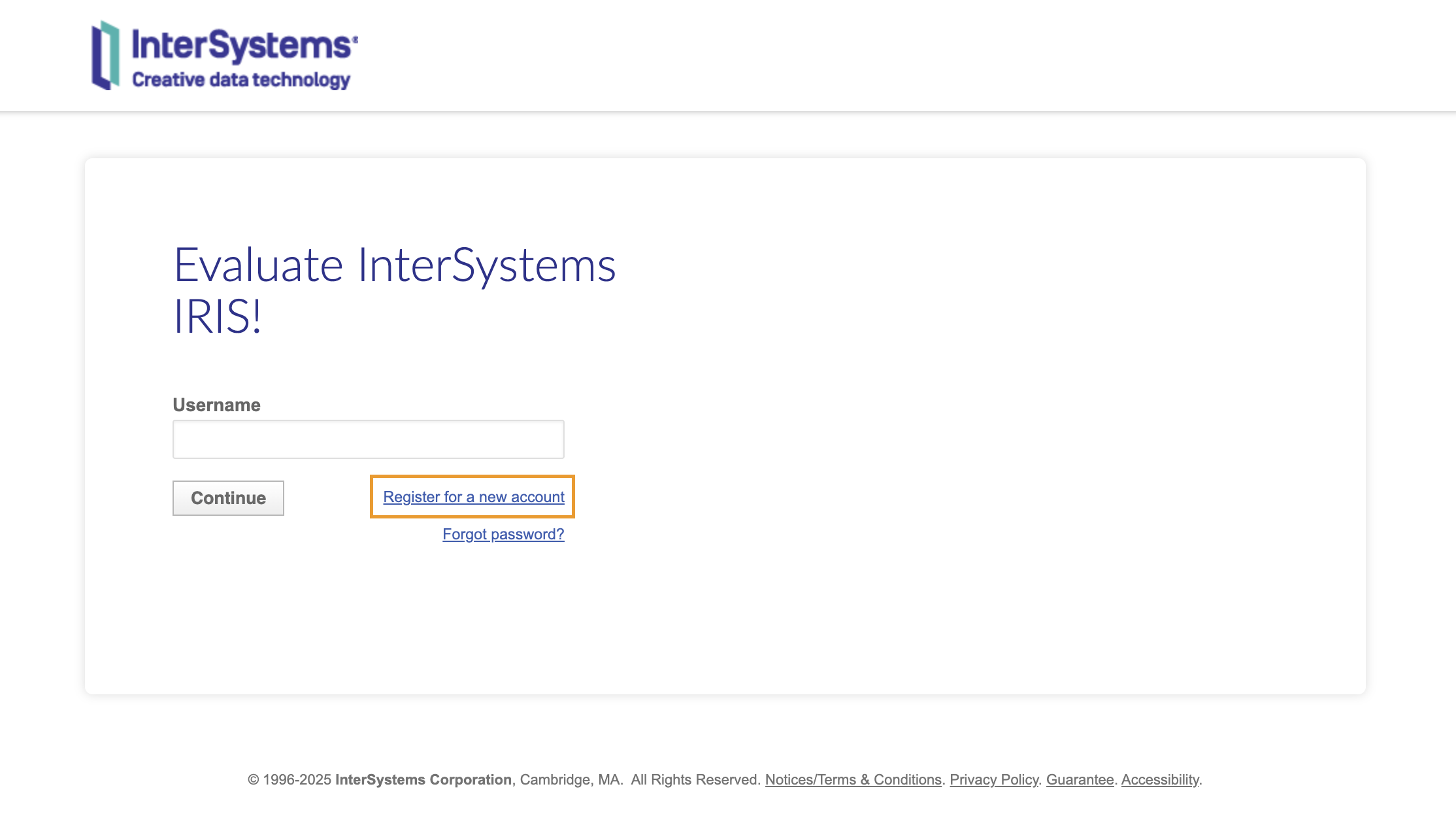 Once you've logged in, you should see the following page; click "Download Community Edition" to begin downloading the install kit:
Once you've logged in, you should see the following page; click "Download Community Edition" to begin downloading the install kit:
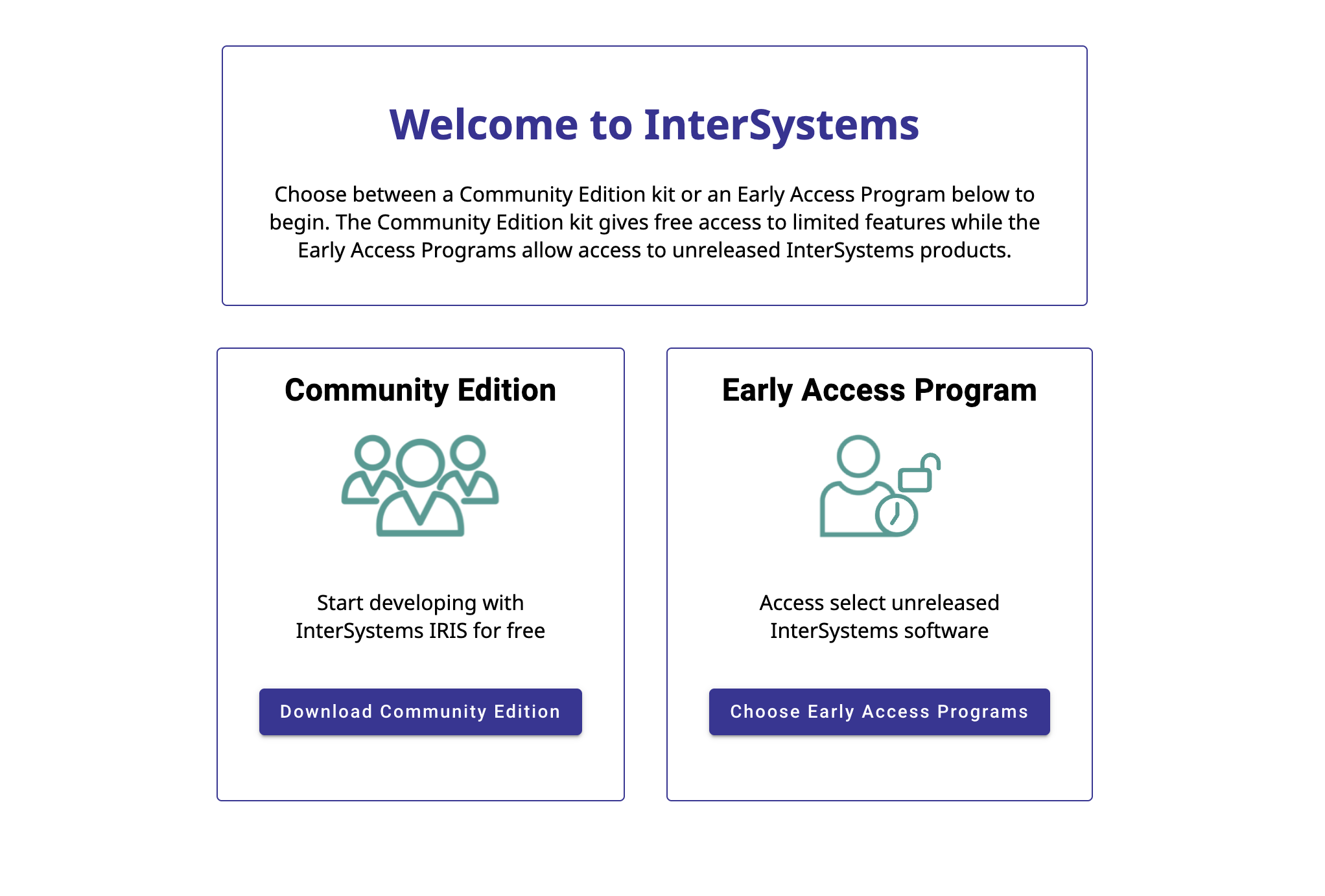
You'll be prompted to fill out some information on exactly which version of InterSystems IRIS you need, and which platform you will be installing it on:
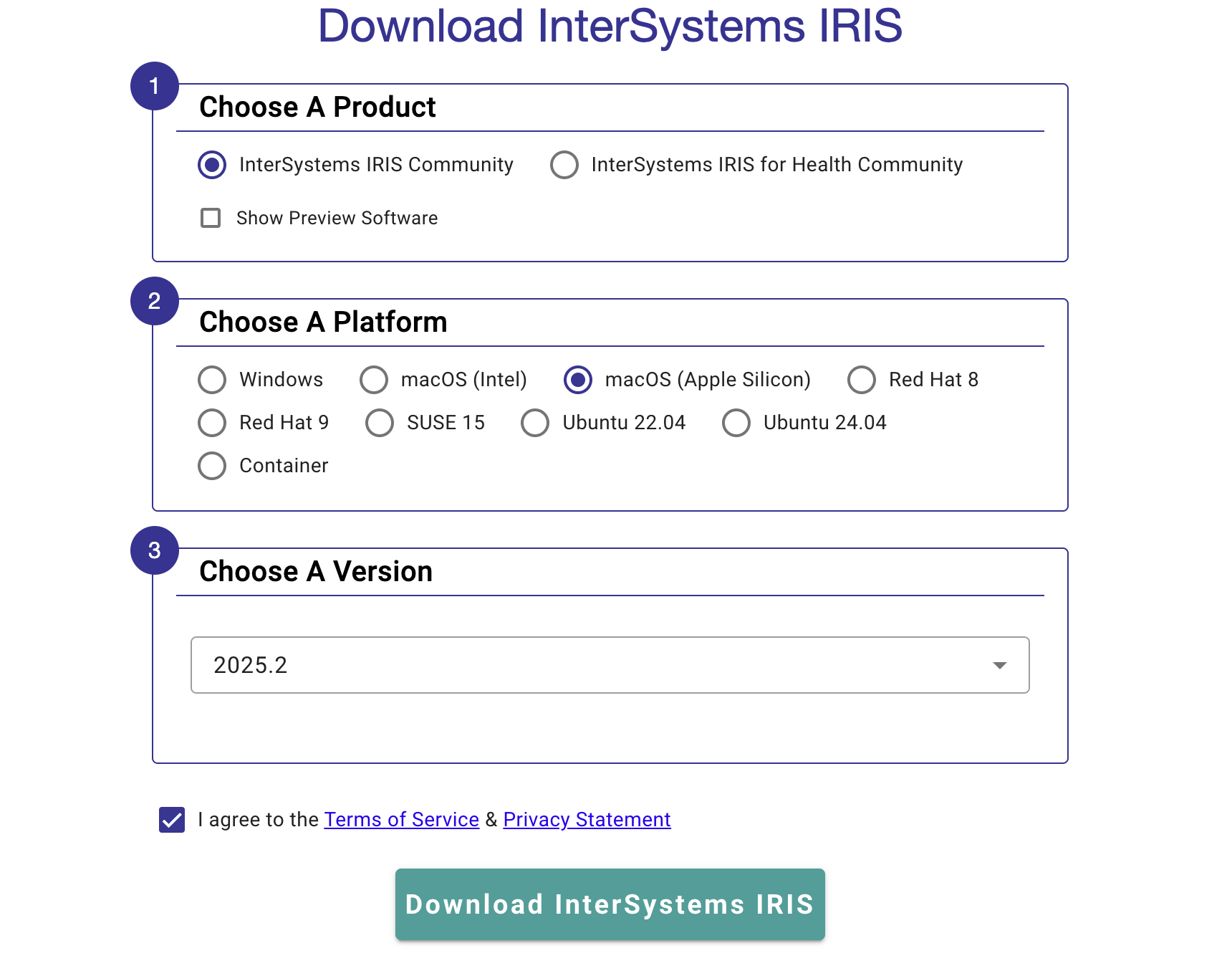
For most use cases, you'll want to select "InterSystems IRIS Community" and the most recent version available for your platform. After agreeing to the TOS, you're ready to download the install kit! Follow the installation instructions in the platform-specific documentation, and you're all set!



 Once you've logged in, you should see the following page; click "Download Community Edition" to begin downloading the install kit:
Once you've logged in, you should see the following page; click "Download Community Edition" to begin downloading the install kit:
