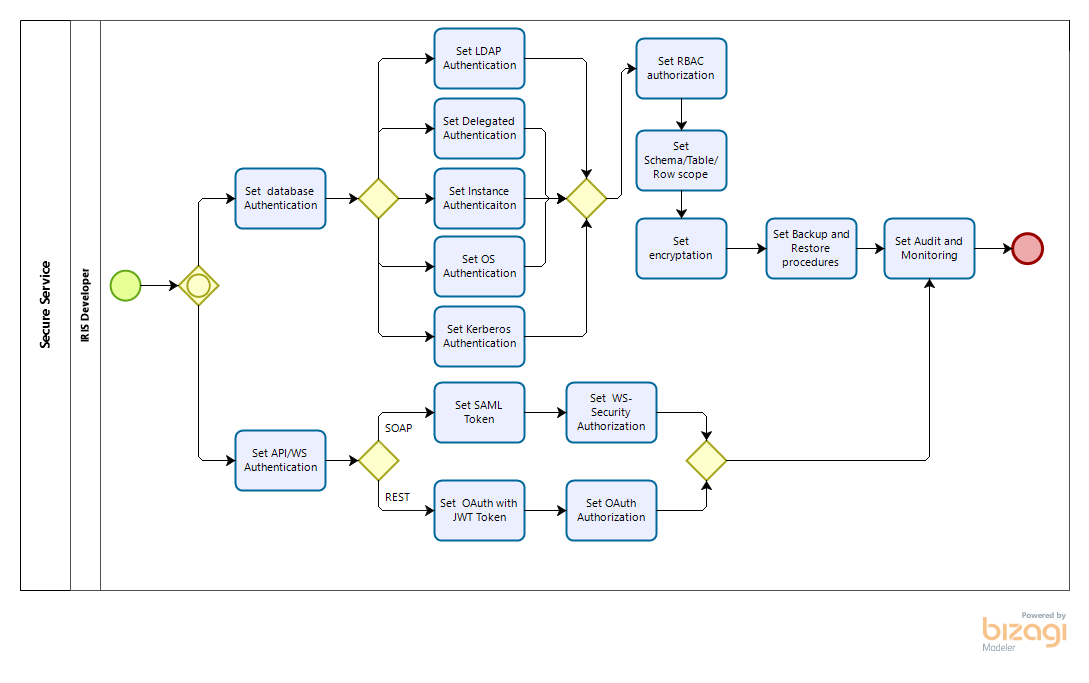
So far, we have covered how to use ObjectScript to manage users, roles, resources, and applications. There are a few other classes in this package that work similarly to the ones mentioned above. However, these four classes are the ones everyone will have to use to manage their application security.