Introduction
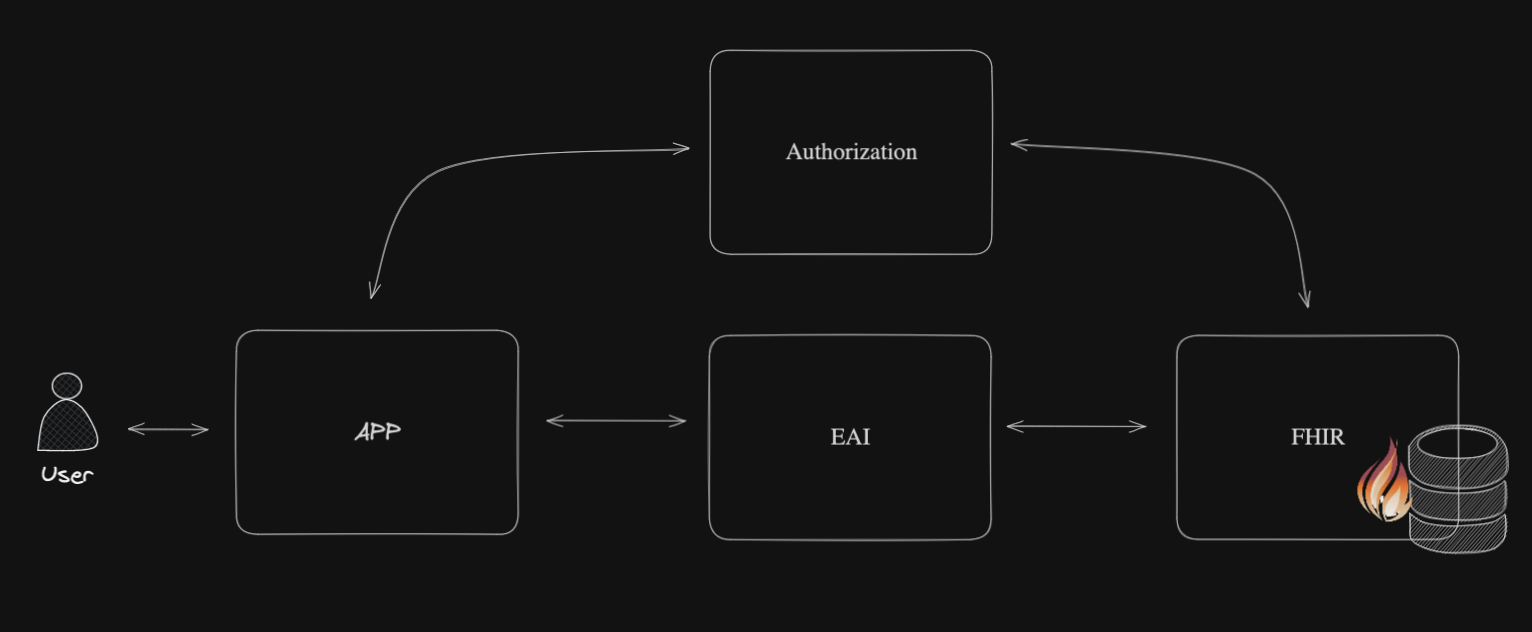
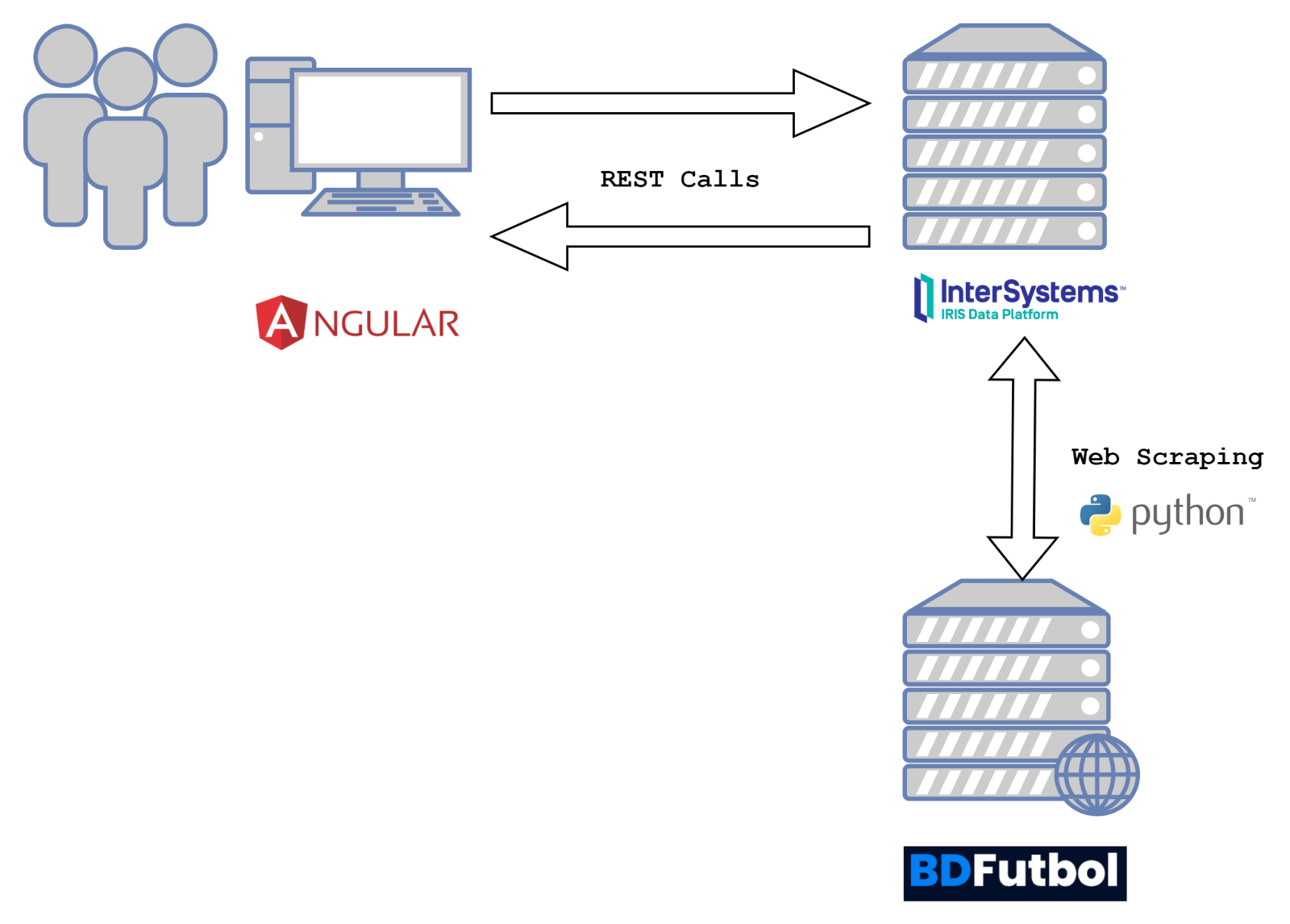
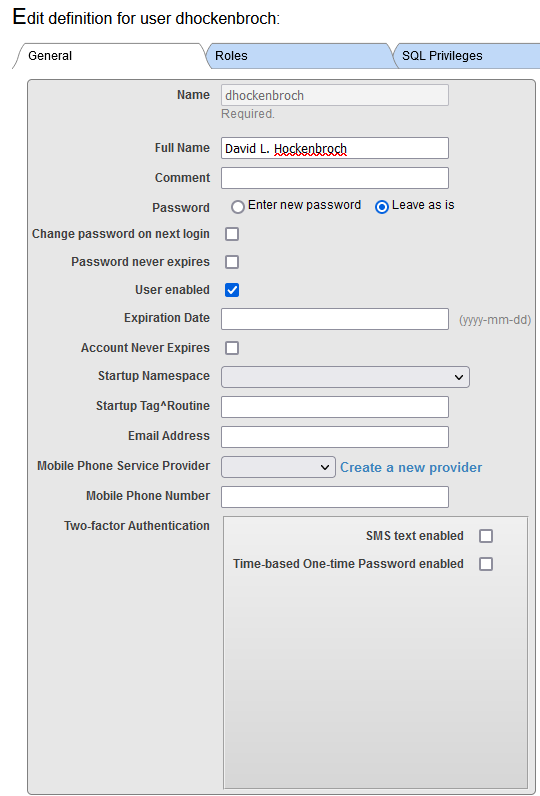
In the modern digital age, securing applications, particularly those handling sensitive health data, is paramount. The confidentiality, integrity, and availability of such data are crucial, necessitating robust security measures. Two-factor authentication (2FA) stands out as a critical enhancement in safeguarding access, adding an extra layer of security beyond just passwords. Recognizing the significance of this feature, InterSystems provides built-in support for 2FA in its database solutions. This tutorial aims to guide you through the process of configuring two-factor authentication in your InterSystems environment, ensuring that your data remains secure and accessible only to authorized users.